The electric power utility industry is in the midst of a transformation. Energy 4.0 technologies, such as the Industrial Internet of Things (IIoT), cloud computing, data and analytics and artificial intelligence and machine learning (AI/ML) are increasingly being implemented to provide utilities with greater visibility and control over the grid.
Collectively, these technologies have the potential to transform how generation, transmission and distribution infrastructure is managed, maintained and modernized.
However, utilities remain hesitant to transition to cloud-based applications that harness the full capabilities of Energy 4.0 technologies. Concerns over cloud security and the risk of regulatory penalties have restricted utilities and limited the full adoption of these new and innovative solutions.
Fortunately, utilities can overcome these challenges by taking a strategic approach to cloud-based applications. By developing cloud security policies and implementing secure IIoT architecture, utilities can enhance performance, optimize operations and maintenance and improve safety all while protecting data and ensuring the reliable flow of power to customers.
On-premises vs. cloud-based IT infrastructure
As technology advances, utilities are faced with an important strategic decision — should they invest in on-premises IT infrastructure or leverage the capabilities of a cloud provider?
While both on-premises and cloud-based IT infrastructure offer advantages and disadvantages, choosing the best approach will depend on the utility, the strategic objectives of the business and the specific application requirements.
On-premises IT infrastructure
On-premises IT infrastructure is built, owned, managed and controlled privately by the utilities. Data centers, servers and other hardware are located on-site while software and applications are installed locally.1
Because it is privately owned, on-premises infrastructure generally allows for greater control. The IT department can tailor the system to meet specific requirements and make upgrades or expand capacity as required. Localized data storage may also be needed to meet regulatory requirements.
However, the utility must also bear the full costs of procuring, deploying, maintaining and upgrading the system over its entire lifecycle, while also managing auxiliary components, real estate and security.
Cloud-based infrastructure
Cloud computing is the delivery of services through the Internet, including data storage, servers, databases, networking, and software.2 Hardware and software reside offsite and are hosted, managed and maintained by the cloud service provider. Multiple organizations may securely share these resources on a pay-per-use basis, scaling access as needed in response to changing business requirements.
Because the utility is not required to build or maintain equipment, cloud computing generally offers a lower upfront cost than on-premises infrastructure. Reputable cloud providers also tend to offer better security, greater resilience and higher performance than most in-house systems due to the size and scale of their business.3
Cloud-based applications
While a utility may use the cloud for their day-to-day operations, in many cases they will be leveraging cloud-based applications from vendors or other strategic partners.
Cloud-based applications provide utilities with access to the vendor’s cloud for specific purposes, such as accessing data from remote monitoring sensors or storing thermal and visual images for future analysis.
Because the vendor has a relationship with the cloud service provider, the utility simply pays to use the service and does not need to build or maintain any internal infrastructure.
The benefits of the cloud
While there may be times when a utility needs to build traditional, on-premises infrastructure, the cloud offers numerous benefits in most situations.
LOWER UPFRONT COSTS
Building an on-premises data center is expensive and requires specialized expertise and experience that may be difficult to attract or develop. Utilities must find suitable real estate, procure equipment and components, design and build the system, run power and cooling infrastructure, implement networking and communications, install and maintain software and ensure everything is fully optimized.
With the cloud, utilities simply pay to access resources on-demand without the burden or costs associated with on-premises infrastructure.
GREATER SCALABILITY
Because demand for IT resources can change, utility-owned data centers must operate at far lower than full capacity most of the time to ensure they can meet peak demand if required. Not only does this increase IT costs, but it also limits flexibility and responsiveness to changes in the business.
The cloud, on the other hand, allows utilities to easily scale resources up or down as needed. This on-demand, pay-as-you-go model makes it easy to add new applications, sensors, facilities or workloads without building capacity or expanding the system.
FEWER MAINTENANCE REQUIREMENTS
Utilities tend to favor upfront capital investments over ongoing operating costs, which may make the idea of an on-premises solution more attractive. However, managing, maintaining and upgrading IT infrastructure still incurs significant operational costs and requires skilled personnel to oversee and maintain.
In contrast, reputable cloud service providers handle these ongoing requirements on the utility’s behalf, reducing overall costs as well as the burden on internal IT departments.
BETTER DISASTER RECOVERY
Storms, fires, floods, power outages and other disasters can destroy IT infrastructure or wipe data from servers, with catastrophic consequences if data is not properly backed up.
Instead, utilities can make use of pre-built backup and disaster recovery tools from cloud service providers that operate numerous data centers and multiple servers.
ROBUST SECURITY
While security is often one of the primary concerns utilities have when considering the cloud, the truth is that most reputable cloud providers can achieve greater security and respond to emerging threats more quickly and effectively than an internal IT team.
Most cloud service providers offer more robust security and pre-built management and policy tools such as multi-factor identification, user and role-based permissions and encryption as standard features.
ACCESSIBILITY
Finally, software or files stored locally can only be accessed by a specific device, limiting collaboration, flexibility and responsiveness. Cloud-based data storage allows utilities to access data and synchronize files between multiple devices, improving decision-making and ensuring data is available when and where it is needed.
ADDRESSING THE BARRIERS TO THE CLOU
Despite the advantages of the cloud, utilities may find that there are barriers to successfully implementing and using cloud-based applications. Many of these barriers are rooted in regulatory and compliance requirements or internal policies and workflows. While some may ultimately restrict utilities from using the cloud in all scenarios, many can be addressed for common applications.
DATA RESIDENCY AND COMPLIANCE
Data residency refers to the localization of regulated data, especially Personally Identifiable Information (PII), within a particular region or country. Many regulators do not allow companies to collect, store or use data outside their home country due to privacy and security concerns.
Similarly, data transit requirements may further state that data cannot transfer through another country or region, which can be especially difficult given the interconnected nature of the Internet.
These regulations can pose challenges for cloud-based applications since cloud providers may have data centers spread across multiple countries.
However, many cloud-based applications do not collect, transmit or store PII or any data that is critical to the flow of electricity. In these cases, the data may be less regulated.
SECURITY CONCERNS
As critical infrastructure, utilities are rightly concerned about cybersecurity threats. Regulated standards enforce cybersecurity defenses, but internal security policies may go even further in limiting the use of network access or services due to perceived security risks.
Cyberattacks have increasingly targeted utilities and other industrial control systems, seeking entry through the least protected links. In fact, the utility sector saw a 46% year-over-year increase in cyberattacks in 2021, averaging 736 attacks per week.4
However, as highlighted above, reputable cloud providers place security as one of the most important areas of their business. And depending on the application, not all data can be useful to malicious actors, mitigating the risk of harm even if it does fall into the wrong hands.
North American Electric Reliability Corporation regulations for remote monitoring systems
The North American Electric Reliability Corporation (NERC) is a not-for-profit international regulatory authority responsible for the reliability and security of the grid.5
NERC regulations define what is considered to be a Critical Asset subject to the Critical Infrastructure Protection (NERC CIP) standards.
According to the NERC document Identifying Critical Cyber Assets Version 1.0, a Transmission Substation is identified as a Critical Asset. ‘Equipment Monitoring’ systems, such as thermal and visual sensors, are identified as a Cyber Asset associated with the Transmission Substation that is “important, but not critical to the Bulk Electric System (BES) operation”.
Given this definition, remote monitoring solutions are not subject to the regulations of NERC CIP 5, allowing the utility to leverage cloud-based applications.6
Note that other countries and jurisdictions may have different regulations. Utilities should always ensure they are compliant before implementing cloud-based applications.
Managing cloud-based applications
As cloud-based applications become more prevalent in the industry, utilities must develop a strategy for selecting, implementing and managing these solutions.
Identify strategic objectives and develop a business case
When choosing a cloud-based application, the first step is to identify the strategic objectives of the project. Define and articulate how the solution aligns with the larger goals of the business, and state the expected outcomes that will determine if the project is successful. Identify project milestones, key performance indicators and other strategic requirements that will shape the rest of the project.
From there, utilities should conduct a more comprehensive business case to determine the viability of the project. Take into account the various costs and benefits of any potential solutions that are being evaluated. For example, for a remote monitoring system, compare the costs of procuring and installing the solution against expected improvements in operations, maintenance, safety, and reliability.
Ensure interoperability
One of the potential challenges when using multiple vendor-driven cloud-based applications is that each vendor may rely on a different cloud provider. It is therefore vital to ensure interoperability and the ability to share and access data from multiple sources within a centralized software or dashboard.
When evaluating potential solutions, ensure they offer APIs, DNP hooks for SCADA or other standard protocols that make it easy to transfer and analyze data between systems. Without these links, utilities can end up with data silos that add complexity and limit the ability of users to view information when needed.
Cloud vendor selection
Finally, utilities should be aware of the potential for vendor lock-in. Fully implementing cloud-based applications can sometimes require time and resources that tie the utility to a specific vendor. Once up and running, switching costs can make it prohibitively expensive or difficult to change to a new solution down the road.
Before making a selection, take the time to ensure the solution is flexible and can meet requirements both now and in the future.
Cloud security policies and architecture for remote monitoring
The cloud is a highly secure alternative to traditional, on-premises infrastructure. However, utilities still need to design effective security policies and architectures when deploying IIoT solutions such as remote monitoring sensors.
Encryption
Despite not being subject to NERC CIP 5 standards, utilities should ensure the IIoT architecture of a remote monitoring solution has comprehensive Transport Layer Security (TLS) encryption and authentication built along every step in the communication. This ensures that data cannot be intercepted and viewed by hackers and that only authorized users have access through two-factor identification. Once stored in the cloud, data should be encrypted using the Advanced Encryption Standard.
Segregation from critical assets
When deploying remote monitoring solutions, utilities should ensure that the IIoT sensors have no electrical or physical connections that may disrupt the operation of the equipment that is being monitored. Infrared technology is an example of a non-invasive, contactless means of measuring temperature on electrical equipment. The sensors should be physically outside the security perimeter as defined by NERC CIP 5, and the sensors and cloud dashboard should have no connection to the Critical Asset communication network.
By segregating the systems, the utility eliminates the risk of infiltration through the IIoT network connection. Further, because the sensors are collecting temperature data and thermal and visual images of equipment, the data itself is not sensitive and cannot be used in any harmful way to disrupt the flow of power.
Cloud vendor security policies and vendor audits
Before deploying any application, the utility should evaluate the vendor’s cloud security policies. Ask how they manage and store data, how much, if any, access employees have to the data and whether they can directly access the sensors. Ask to see their security policies, and ensure they are willing and able to answer questions about their cloud provider and the measures they take for security.
Many utilities will take this a step further by conducting a detailed vendor audit before working with a vendor. This provides a complete understanding of the vendor and makes it possible to identify potential vulnerabilities before selecting a technology.
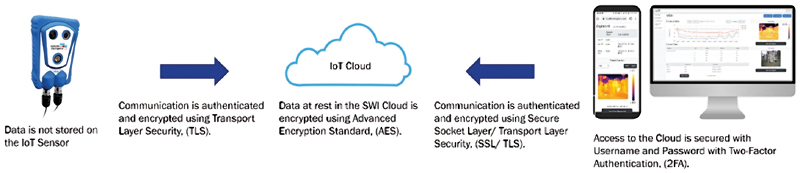
Figure 1. IIoT Architecture shows the communication paths and security measures that are used on each step. Note that the IIoT network is outside of the utility security perimeter.
Ongoing user training
While it may seem low-tech, many attacks on utilities actually come in the form of phishing emails, malware-laden attachments or infected links.7 These behavioral attacks have become more sophisticated and can be extremely effective if employees are unaware or unsure of what to look out for.
Frequent user training helps employees recognize potential security threats and identify suspicious emails or links. By continuously improving the security knowledge of team members, utilities can mitigate the risk of infiltration.
A strategic approach to cloud-based applications
Energy 4.0 technologies will play an increasingly large role in the electrical utility industry. As more organizations embrace the Industrial Internet of Things, cloud computing, data and analytics and artificial intelligence and machine learning, the electric grid will become more flexible, responsive and reliable.
Thermal and visual monitoring systems are one example of a cloud-based application that can significantly improve utility operations. By providing greater visibility and control over high-value critical assets and components, remote monitoring solutions make it possible to transition away from physical inspections toward a Condition-Based Maintenance strategy without the need for costly IT and networking infrastructure.
Faced with rising complexity and pressure to deliver affordable and reliable power to customers, utilities cannot let the fear of the cloud limit their capabilities. Through effective cloud-security policies and architectures and relationships with vendors that understand the unique security requirements of the industry, utilities can effectively implement cloud-based applications that lower costs, improve scalability and performance and deliver a better experience to both customers and internal teams.
 Richard Harada has more than 20 years of experience in industrial networking communications and applications. Prior to joining Systems With Intelligence, Harada worked at RuggedCom and Siemens Canada, where he focused on product management and business development for industrial communications in the electric power market. Harada is an electronic engineering technologist and has a Bachelor of Science degree in computer science from York University in Toronto.
Richard Harada has more than 20 years of experience in industrial networking communications and applications. Prior to joining Systems With Intelligence, Harada worked at RuggedCom and Siemens Canada, where he focused on product management and business development for industrial communications in the electric power market. Harada is an electronic engineering technologist and has a Bachelor of Science degree in computer science from York University in Toronto.
 John Nam has more than 20 years of experience developing high-tech hardware and software products. As the head of Engineering at Systems With Intelligence, Nam is responsible for the research and development of new products and solutions. He holds a Bachelor of Science degree in electrical engineering and has a Ph.D. in engineering physics from McMaster University.
John Nam has more than 20 years of experience developing high-tech hardware and software products. As the head of Engineering at Systems With Intelligence, Nam is responsible for the research and development of new products and solutions. He holds a Bachelor of Science degree in electrical engineering and has a Ph.D. in engineering physics from McMaster University.
1 https://www.hpe.com/us/en/what-is/on-premises-vs-cloud.html
2 https://www.investopedia.com/terms/c/cloud-computing.asp
3 https://www.infosysbpm.com/newsroom/analyst/documents/next-gen-it-services.pdf








